Introduction.
TCP / IP.
TCP / IP was developed and introduced by the US Department of Defense in 1972 and was applied in ARPANET(TOdvanced Rsearch Projects TOgency Network), which was the Department of Defense wide area network as a means of communication for the different US agencies The transition to TCP / IP in ARPANET was completed in 1983.
It is known as internet protocol family to the set of network protocols that are implemented by the protocol stack on which the Internet is based and that allow the transmission of data between computer networks.
The two most important protocols, and which were also the first to be defined and also the most used, areTCP (Transmission Control Protocol or Transmission Control Protocol) e IP (Internet Protocol or IinternetProtocol), hence it is also called TCP / IP Protocol Suite. The types of existing protocols exceed one hundred, among which we can mention HTTP, FTP, SMTP, POP, ARP, etc. as the best known.
TCP / IP is the platform that supports the Internet and that allows communication between different operating systems on different computers, either over local area networks (LAN) or wide area networks (WAN).
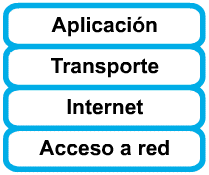
Stack levels.
Currently, the discussion continues regarding whether the five-level TCP / IP model fits within the OSI model (Open Systems Interconnection or ORpenSystems Interconnection) of seven levels.
|
Model |
Levels |
|---|---|
|
TCP / IP |
5 Application |
|
OR IF |
7 Application |
TCP / IP model.
It uses encapsulation to provide abstraction of protocols and services to different layers in the stack. The stack consists of five levels:
|
Level |
Name |
Description |
|---|---|---|
|
5 |
App. |
It is made up of various service protocols such as:
Routing protocols like BGP (Border Gateway Protocol) and RIP (RoutingInformation Protocol) that use transport by TCP and UDP respectively can be considered as part of this layer. |
|
4 |
Transport. |
It is made up of various service protocols such as:
Protocols like OSPF (ORpen Shortest Path First), which run over IP, can also be considered as part of this layer. ICMP (Iinternet Control Message Protocol) e IGMP (IinternetGroup Management Protocol) that also use IP can be considered part of the Network Layer. |
|
3 |
Net. |
It is made up of various service protocols such as IP (including IPv4 and IPv6). Protocols likeARP (TOddress Resolution Protocol) and RARP (Reverse TOddress Resolution Protocol) operate below IP, but above the Link Layer, so they belong somewhere between the Network Layer and the Link Layer. |
|
2 |
Link. |
Composed of protocols such as:
|
|
1 |
Physical. |
Physical environment. |
The highest closest levels are closest to the user, while those further down are closest to the physical transmission of the data. Except for obvious reasons in the first and last levels, each level has an upper level and a lower level that, respectively, either use a service of the level or provide a service. An abstraction method to understand this is to look at the tiers as providers or consumers of services. Example: TCP at the transport level requires a network level protocol, such as IPv4, which in turn requires a link level protocol, with TCP being a service provider for application level protocols.
Application level.
It is the level that most common network programs use to communicate over a network. The communication that occurs at this level is specific to the applications and the data transported from the program is in the format used by the application and is encapsulated in a protocol of the Transport level. Since the TCP / IP model does not have intermediate levels, the Application level must include any protocol that acts in the same way as the protocols of the Presentation Level Y Session level of OSI model. The most commonly used Transport Layer protocols are TCP and UDP, which require an available, service-specific port for servers and ephemeral ports. Although routers and switches do not use this level, bandwidth-controlling applications do.
Transport level.
This level mainly provides what is necessary to connect integer applications through ports. While IP (Internet Protocol), of the Network Layer, provides only the best form of delivery, the transport layer is the first layer that takes care of the reliability. Among all the protocols of this level, both TCP and UDP are used to transport a large number of high-level applications. Applications at any level are distinguished by the TCP or UDP ports they use.
-
TCP.
-
The best example of this level is TCP, which is a connection-oriented protocol that solves numerous reliability problems to provide a reliable transmission of bytes since it ensures that the data arrives in order, has a minimum of error corrections, is discard duplicate data, resend lost or dropped packets, and include traffic congestion control.
Connections through TCP have three phases:
-
Establishing the connection.
Before the client tries to connect to the server, the latter must first bind to the port to open it for connections, that is, a passive opening. Once established the client can start the active opening. A three-stage greeting is required:
- Active opening is done by sending a SYN packet (synchronize) to the server.
- In response, the server responds with a SYN-ACK (sync shaping) packet.
- Finally the client sends an ACK (confirmation) packet back to the server.
At this point both client and server have received a confirmation of the connection.
-
Data transfer.
There are three key functions that differentiate TCP from UDP:
- Error-free data transfer.
- Orderly data transfer.
- Retransmission of lost packets.
- Discarded duplicate packets.
- Adjustment in data transmission congestion.
-
Connection termination.
This stage uses a three-way hello, with each end of the connection terminating independently. When one end wants to stop its part of the connection, it sends a FIN packet, which the other party confirms with an ACK packet. Therefore a connection interruption requires a pair of FIN and ACK packets from each side of the TCP connection.
A connection can be left half open when one end has terminated the connection from its side but the other end has not. The end that terminated the connection can no longer send data on the connection, but the other end can.
The most common method is a three-stage hello where host A sends a FIN packet and host B responds with a FIN packet and an ACK (in the same step) and host A responds with an ACK packet.
TCP performs the following steps on its socket:
- LISTEN
- SYN-SENT
- SYN-RECEIVED
- ESTABLISHED
- FIN-WAIT-1
- FIN-WAIT-2
- CLOSE-WAIT
- CLOSING
- LAST-ACK
- TIME-WAIT
- CLOSED
LISTEN represents the connection waiting for requests from any remote TCP port. SYN-SENT represents the remote TCP waiting to send back the TCP packet setting flags SYN Y ACK. SYN-RECIVEDrepresents waiting for the remote TCP to send the confirmation back after it has sent back another connection confirmation to the remote TCP (set by the TCP server). ESTABLISHED represents that the port is ready to receive / send data from / to remote TCP (both TCP clients and servers do). TIME-WAITrepresents the wait time required to ensure that the remote TCP has received confirmation of its connection termination request.
-
-
UDP.
-
UDP, sometimes sarcastically referred to as Unreliable Datagram Protocol (Unreliable Datagram Protocol), is an uncorrected datagram protocol; does not provide the guarantee of reliability and orderliness of TCP to the protocols of theApplication Level and datagrams can arrive out of order or get lost without notification. As a consequence of the above, UDP is a faster and more efficient protocol for light or time-sensitive tasks, providing a very simple interface between the Network level Y Application Level. If some kind of reliability is required for the transmitted data, it must be implemented at the upper levels of the stack.
Like IP, and unlike TCP, it is a best-effort or unreliable protocol. The only reliability problem that it solves is the correction of errors in the header and data transmitted through a 16-bit field to checksum (checksum), a form of redundancy control in order to protect the integrity of data by verifying that it has not been corrupted.
The UDP packet structure consists of 4 fields.
- Port of origin. Responsible for identifying the port that sends and that is assumed to be the port to which the response is sent if needed. This field is optional: if not used, the value of the field must be 0.
- port of destination. Identify the destination port. It is mandatory.
- Length. A 16-bit field that specifies the length of the entire datagram: header and data. The minimum length is 8 bytes since it is the length of the header itself.
- Checksum. A 16-bit field used to check for header and data errors.
The most common applications that make use of this type of protocol are DNS, streaming media applications, Voice over IP (VoIP), TFTP, and online games.
-
SCTP.
-
SCTP is a reliable transport mechanism oriented towards connection. It is also oriented towards data transmission but it is not oriented towards bytes like TCP. Provides multiple transmissions distributed over the same connection. It can also represent a connection with multiple IP addresses so that if one IP fails, the connection is not interrupted. It was initially developed for telephony applications but can be used in other applications.
-
DCCP.
-
DCCP is in the development phase and under the tutelage of the IETF (Internet Engineering Task Force) which aims to provide the TCP flow control semantics and the UDP datagram service model for the user.
-
RTP.
-
RTP is a datagram protocol that was designed for real-time data such as video and audio transmission. It is a session level that uses the UDP packet format as a basis. However, it is considered that it could accommodate below the transport level of the TCP / IP model.
Network level.
This level solves the problem of capturing data through a single network. IP (Iinternet Protocol) performs the basic task of capturing data packets from a source to a destination. IP can carry data for a large number of top-level protocols (Transport Layer). Another example of a protocol of this level is X.25, which is a set of protocols for WAN networks using telephone lines or ISDN system.
Link level.
This level is not really part of the TCP / IP Protocol Suite, rather, it is the method used to pass packets from the Network Layer over two different hosts. This process can be controlled through the programmatic used as a device driver for a network card as well as on theFirm programming (Firmware) or auxiliary integrated circuits (chipsets). These processes will perform data link functions such as adding a packet header to prepare for transmission, and then transmitting the whole over a physical medium.
This level is where packets are intercepted and sent to a Virtual Private Network (VPN). When this is done, the Link Layer data is considered as the application data and proceeds down the TCP / IP model stack to perform the actual transmission. At the receiving end, data goes up the TCP / IP model stack twice, once for the VPN and once for routing.
Physical level.
Like the Link Level, it is not really part of the TCP / IP Protocol Suite. It considers all the physical characteristics of communication such as the nature of the medium, details of connectors, channel code and modulation, signal strengths, wavelengths, synchronization and lifetime and maximum distances.
OSI model.
The TCP / IP Protocol Suite (and its corresponding stack) have been used before the OSI (Open Systems Interconnection or ORpen Systems Interconnection) and since then the TCP / IP model has been compared to the OSI model both in books and in educational institutions. Both are related but are not comparable. The OSI model uses seven levels, while the TCP / IP model uses five levels. The two levels that make the difference in the OSI Model are the Presentation Level and the Session level, which could be equivalent to Application Level of the TCP / IP model.
Like the TCP / IP model stack, the OSI model is not diverse enough at the lower levels to encompass the true capabilities of the TCP / IP Protocol Suite. A clear example is that an intermediate level is missing to accommodate between the Network level and the Transport level in order to determine where the ICMP and IGMP protocols correspond, and another intermediate level between the Network level and the Transport level to determine where the ARP and RARP protocols correspond.
|
Level |
Name |
Description |
|
7 |
App |
HTTP, SMTP, SNMP, FTP, Telnet, SIP, SSH, NFS, RTSP, XMPP (ANDxtensile Messaging andPresence Protocol), Whois, ENRP Telnet. |
|
6 |
Presentation |
XDR (ANDxternal Dtie Representation), ASN.1 (TObstract Syntax Notation 1), SMB (Server MessageBlock),AFP (TOpple Filing Protocol), NCP (NetWare Cpray Protocol) |
|
5 |
Session |
ASAP (TOggregate Server TOccess Protocol), TLS, SSH, ISO 8327 / CCITT X.225, RPC (RemotePrubbing Call), NetBIOS, ASP (TOppletalk Ssession Protocol), Winsock, BSD sockets |
|
4 |
Transport |
TCP, UDP, RTP, SCTP, SPX, ATP, IL |
|
2 |
Data link |
Ethernet, Token ring, HDLC, Frame relay, ISDN, ATM, 802.11 WiFi, FDDI, PPP |
|
1 |
Physical |
It defines all the physical and electrical specifications of the devices, such as pinouts, voltages, wiring specifications, hubs, repeaters, network adapters, etc. Cable, Radio, foptical fiber, Net for pigeons. |
Levels 7 through 4 are classified as host levels, while levels lower levels 1 to 3 are classified asmedia levels.
Fountain:
http://unidadlocal.com/












No Comment